Flawed Facebook Passwords
How it came to be that Facebook chose to make your password 94x weaker than it need be
There's truth to that statement, there's also a lot of background information I'll cover so you understand it, inside and out. As I covered in my encryption post, I described the process wherein a password input by the user is scrambled up. This process is one way and it's called hashing. I like to think of it as "hash-browns". You take a potato, and you scramble it up, and make something completely new. Another way to think of it is "rehashing" like when you "rehash" a project you've done, again, turning it into something new.

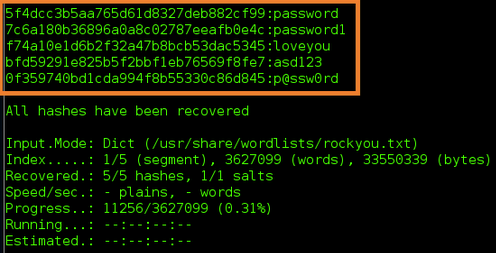
Consider the following hashes created using MD5[1]:
password becomes: 5F4DCC3B5AA765D61D8327DEB882CF99
PASSWORD becomes: 319F4D26E3C536B5DD871BB2C52E3178
PASSword becomes: 64BEBDCE805A0EBE778B88E632B77042
passWORD becomes: B291559957FFC706FC38D49B5512055C
Few things to note. Hashes are always the same length and wildly change despite the input changing only ever so slightly. They also create the same hash every time. Remember how I said hashes are one way? Hashing is "simply"[2] a lot of math that can reliably produce hashes. The math is set up such that even if you steal a hash, you can't calculate the original password that created it.
Surely you've heard of "brute force attacks". That's what hackers do with hashes. If they have a hash, they go "does the hash of aaaaaaaa equal the hash I have stolen", "what about aaaaaaab", until they've tried every permutation. I'll rehash (bad dum tish) how hashing and passwords go hand in hand.
This is how passwords are stored. When you create an account. The service does not save the password but rather, the hash of your password. Then, when you log in, the service hashes your plain text password and then compares the hash to the one saved in the database. Passwords aren't compared, only the hashes. If they match, then you've got the correct password and you'll be signed in.
Facebook's password database will be a table with two columns, and billions of rows. The first entry may read JohnSmith1 : D03A2AB540E8AACF18BBAFC12C4F1569. It's for this reason that Facebook, or whomever, can't send you your password when you forget it. Facebook simply does not store your password, and yet it checks it to log you in. When you enter your password on Facebook, it has to redo all the math and then can compare hashes (which is NP)[3]. Hot PSA: if a website or service or app ever sends you your password in an email or by SMS or whatever... run... run farrrrrrrrrrrr away[4]. The only way that's possible is if they store passwords (not hashed) which is a HUGE security nono.
With that background information out of the way, here's the strange design decision that I discovered Facebook uses. Log out of Facebook, then log in again, BUT, log in with your password in uppercase. You would be logged in. Try this on ANY other service / app / website, it will say your password is incorrect. Turns out, Facebook stores four hashes for each user. Your regular password hash, your password in lowercase hash, your password in uppercase hash and your password in reversed case hash. In other words, if my password were PASSword, I'd be an idiot. If your password is password, you're the reason I have job security. With my password PASSword, as explained before, these passwords would also log me in to Facebook: password, PASSWORD and passWORD.
Entropy: A measure of the disorder or randomness in a closed system. - Wikipedia (now referenced by courts!)
Entropy. Here, it's how complex your password is. I'm sure you've come across hundreds of places that say "you need at least one number" or "you need at least one special character" or "you need at least 10 characters" or "you need at least one capital" (which is strange because my password: canberra didn't work (yes that was a joke (yes, me having to tell you it was a joke shows just how bad it was (how many nested parentheses are grammatically legal?))). All these requirements are to boost your passwords entropy, to make it more complex, to make it harder to guess.
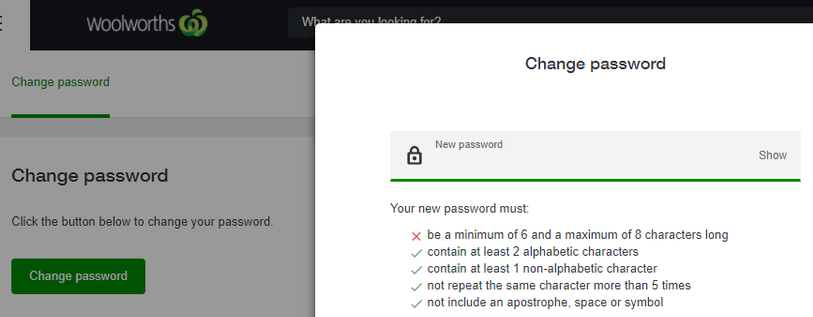
Facebook lets you use the following characters to construct your password: #abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789~!@$&()[5] (which has got to be a contender for the worst hashtag ever). Each character in your password could be any one of those 60 characters. So to calculate the number of possible passwords that are 8 characters long, we simply do 60^8 = 167961600000000. But hang on, we know that Facebook will let you in with a lowercase password, so we can remove the capitals from the character set. Now there are only 34 possible characters in each position. With 34 characters and a password of 8 characters, the number of possible passwords is now 34^8 = 1785793904896. 167961600000000 / 1785793904896 ~= 94. Facebook passwords eight characters long are 94 times weaker than they should be. This becomes 15610x weaker for 16 character passwords!
Facebook's justification is that if you've accidentally left caps lock on, but still got your password right, it didn't want to bother you, so it just lets you through. It's an interesting implementation, I suppose it has its merits, it's just highly unconventional. Security is and always will be a game of security vs usability. You could have 100 length passwords for each website and be super secure, but you'll also be sitting there for 10 minutes just to log in.

Security leaders have recently started recommending you have passphrases rather than passwords. JF*)#gbh takes 3 hours to crack. correct horse battery staple takes 15 octillion years and $ally had a little LAMB! takes 21 octillion years. Those times are for conventional computers. We now have working quantum computers that in the wrong hands will destroy all protections the internet currently employs to secure data. So stay tuned for whatever follows from that!
Otherwise, don't forget to set good, unique passwords, and next time you log into Facebook, why not give an uppercase version of your password a go?