Encryption
The basis of the internet and why it's no excuse to check your banking information on a public network, even if it's salty
"The world’s most valuable resource is no longer oil, but data - The Economist"
It's no secret that companies want your data, and will fight tooth and nail to get it. Those ads in your instagram feed or on sites you visit aren't just there to get you to buy things. But to track you[1] . Whenever you visit a website, you're giving away your location[2] (there's a demo here), full name[3], and all the devices on your network[4]. It's then trivial to find your date of birth, a photo of you and your phone number through Facebook, where you work through Linkedin, sky's the limit. And there we have it, identity theft baby! These searches can be done enmass too, for example, with one command, I can find all the people that work at Microsoft.
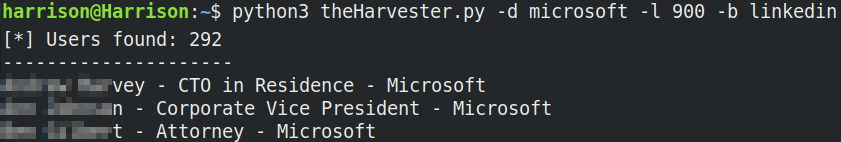
I think it's safe to say that we've now reached a point of learned helplessness where all this information of ours is public and there's not much we can do about it. You're largely right, but the rest of your data is relatively safe. Let me explain.
Encryption
Most data sent today is encrypted. Encryption essentially takes plain data and converts it to garbage so the information becomes unreadable. Encryption is useless if we can't unscramble it and get the original information back. This is called decryption.
Say we have the data G'day mate and we encrypt it with a method where we substitute each character with the next letter in the alphabet (a becomes b, b becomes c...)[5], so our message becomes H'ebz nbuf, with no knowledge of how the data was encrypted, this information becomes useless to us. But, if the receiver knows how to decrypt this data (or replace each character with the one before it) the receiver can decode the message and get the original data.
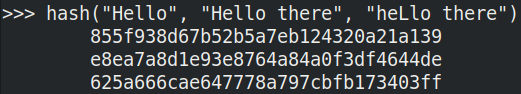
Hashing converts data into a short character sequence. Hello turns into 8b1a9953c4611296a827abf8c47804d7 and Hello there turns into e8ea7a8d1e93e8764a84a0f3df4644de. Notice how these are the same length? What about if we hash heLlo there? You'd expect the hash to be somewhat similar? Wrong: 625a666cae647778a797cbfb173403ff. Hash functions are complex mathematical equations (have a look here if you're game) that generate a wildly different hash depending on the input to secure your data better. Hashing does not store the original data but generates a "summary" or "imprint" of the data to check against.
This is how passwords are stored. When you create an account. The service does not save the password but rather, the hash of your password. Then, when you log in, the service hashes your plain text password then compares the hash to the one saved in the database. Passwords aren't compared, only the hashes. If they match, then you've got the correct password and you'll be signed in. This is great, but there are websites that host cracked hashes behind common passwords. So if the service has its database hacked (which sadly often happens), it doesn't take programmers long to retrieve the passwords from the hashes in the leak. If your email and hashed password are in the leak, and you use the same password at this service at your email, well there goes your email!
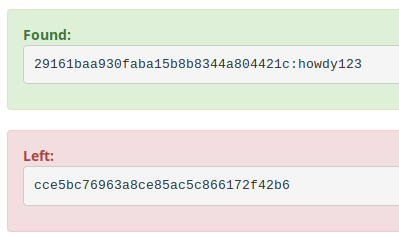
Salting is hashing, but protects you from already discovered hashes. Salting basically adds a password to your password. If my password to bookface is howdy123, hashed, that becomes 29161baa930faba15b8b8344a804421c, which I can search for online and get my original password. But if bookface adds their salt, my password becomes bookface's_secret_salt_howdy123 and the hash: cce5bc76963a8ce85ac5c866172f42b6, which won't be listed anywhere on the internet. I'd have to then crack it myself which is prohibitively expensive. Ideally all the services you use are hashing and salting your passwords.
Can I check banking on public WiFi?
If this was 5 years ago I'd strongly suggest you didn't. If this was today, I'd still suggest you didn't, but it's far better than it was. I'm sure you've heard the notion that the guy in the hoody at your cafe is listening to all the data that goes over the unprotected network. Well you're correct. HTTP powers the internet. It's how computers talk to each other. HTTP started in 1991 back when they weren't thinking of hackers. HTTP is super insecure. It's trivial for me to open free software, listen to traffic on the network, pull out passwords that you're sending to your bank or pictures you're looking at. Nowadays all websites should be using HTTPS, it's HTTP but with encryption, which, remember, scrambles your data.
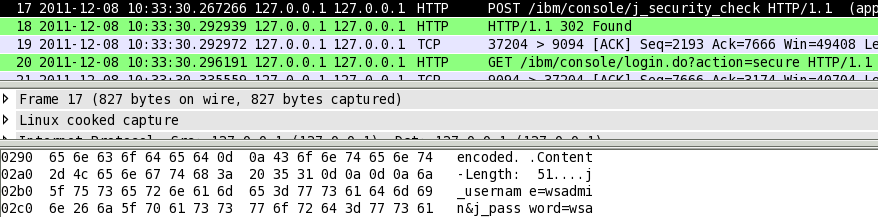
This bit of data was sniffed from the air off public wifi, and because this data was encoded with HTTP, the password can be seen unencrypted
I say you still shouldn't access your banking on public networks because if you own the network, you can see everything, even your bank password behind HTTPS[6]. But what if you trust your cafe not to store your password? Well those hoodie hackers are now instead of listening to traffic, pretending to be the cafe wifi and forcing your device to connect to it so that they still end up with your bank password[7]. Your devices are getting smarter and detecting these types of attacks and warning you about them. They're also enabling encryption by default, so you're well protected, but there are a few things you can do to ensure you're more secure than the person next to you so that they become the favoured target.
- Use a strong password, and by strong, I mean long.
F*(fwa#$takes 3 hours to decode butmy frogzz need metakes 10 billion years. Try your password here and check if it's ever been a part of a data breach here - Use different passwords for different places. Use a password manager for this
- Keep your software up to date so that security holes can be fixed
- Make sure you see a green padlock in your browser URL bar when submitting information on the web (this tells you you're using HTTPS)
- But the best offense is defense. Simply reduce the information you put up online. That or live off the grid...