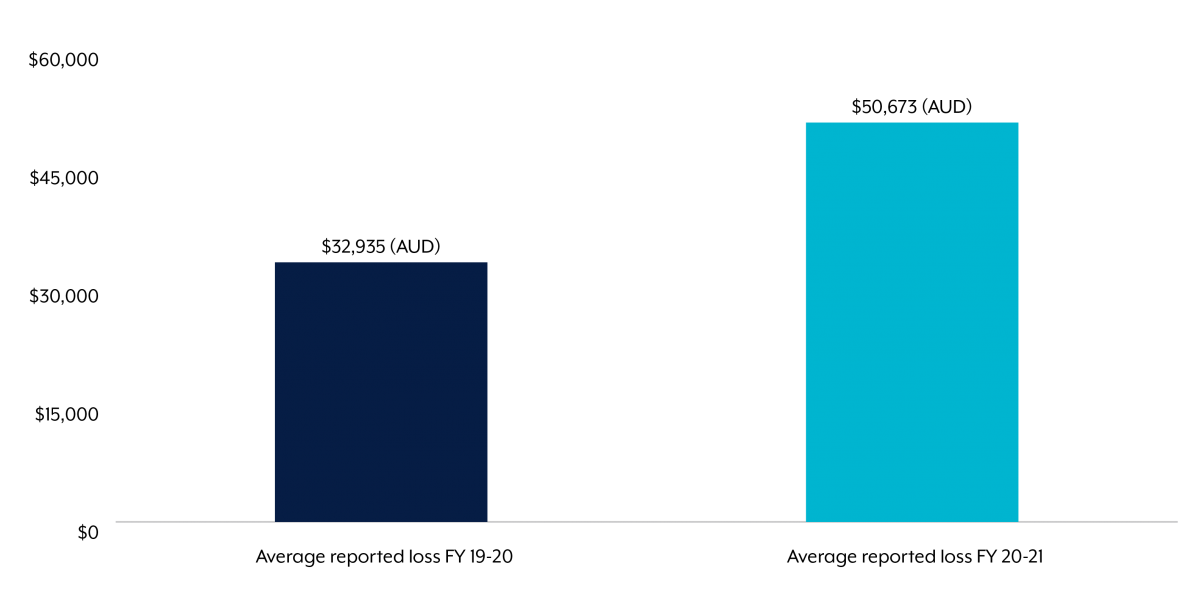Australian Business Email (In)security
A small investigation reveals Australian business emails are ripe for attack
Email spoofing is as rampant as ever, as it usually nets quick results for scammers as they piggy-back off the trust of well-known institutions. By design, the Internet's email delivery protocol allows any mail server to claim to be any other company's mail server. If it weren't for SPF, DKIM & DMARC, I could send emails from [email protected] or [email protected] (if I were happy to commit fraud).
SPF and DMARC in particular are frighteningly easy to implement as it simply involves adding two DNS TXT records to a domain, and instantly it's forever protected against (most)[1] spoofing attacks (maintenance withstanding).
I aim to answer one question: What proportion of Australia's most visited 3,000 domains perfectly implement SPF and DMARC to prevent mail spoofing?
What's SPF and DMARC exactly?
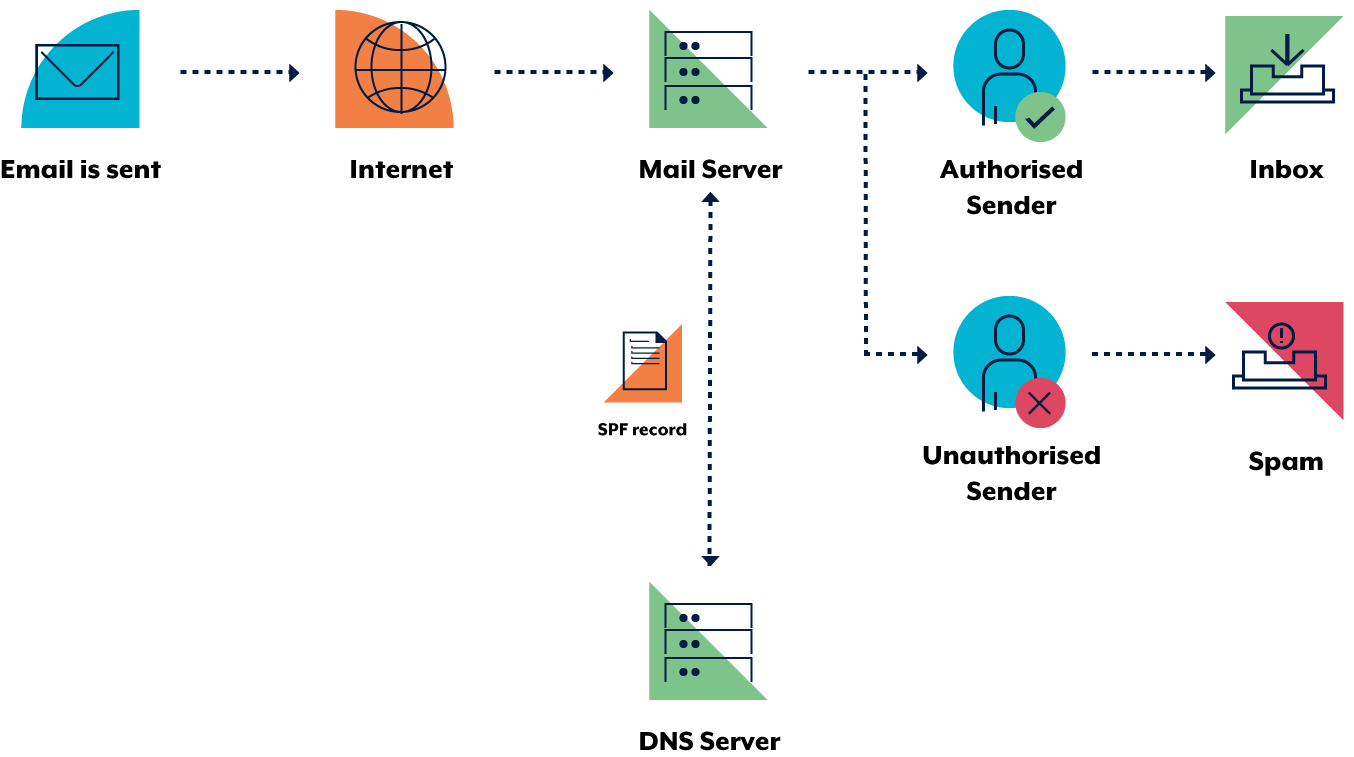
Put simply, SPF (Sender Policy Framework) dictates which mail servers (or IPs) can send mail for that domain. For instance, I use gmail for my email here on harrisonm.com, so my SPF record says only Google IPs can send mail on behalf of harrisonm.com. If a scammer pretends to send mail for harrisonm.com from their mail server, the mail client that receives the spoofed mail will look up the SPF TXT record at harrisonm.com, see that the spoofing mail server's IP doesn't match Google's IPs, and reject the mail.
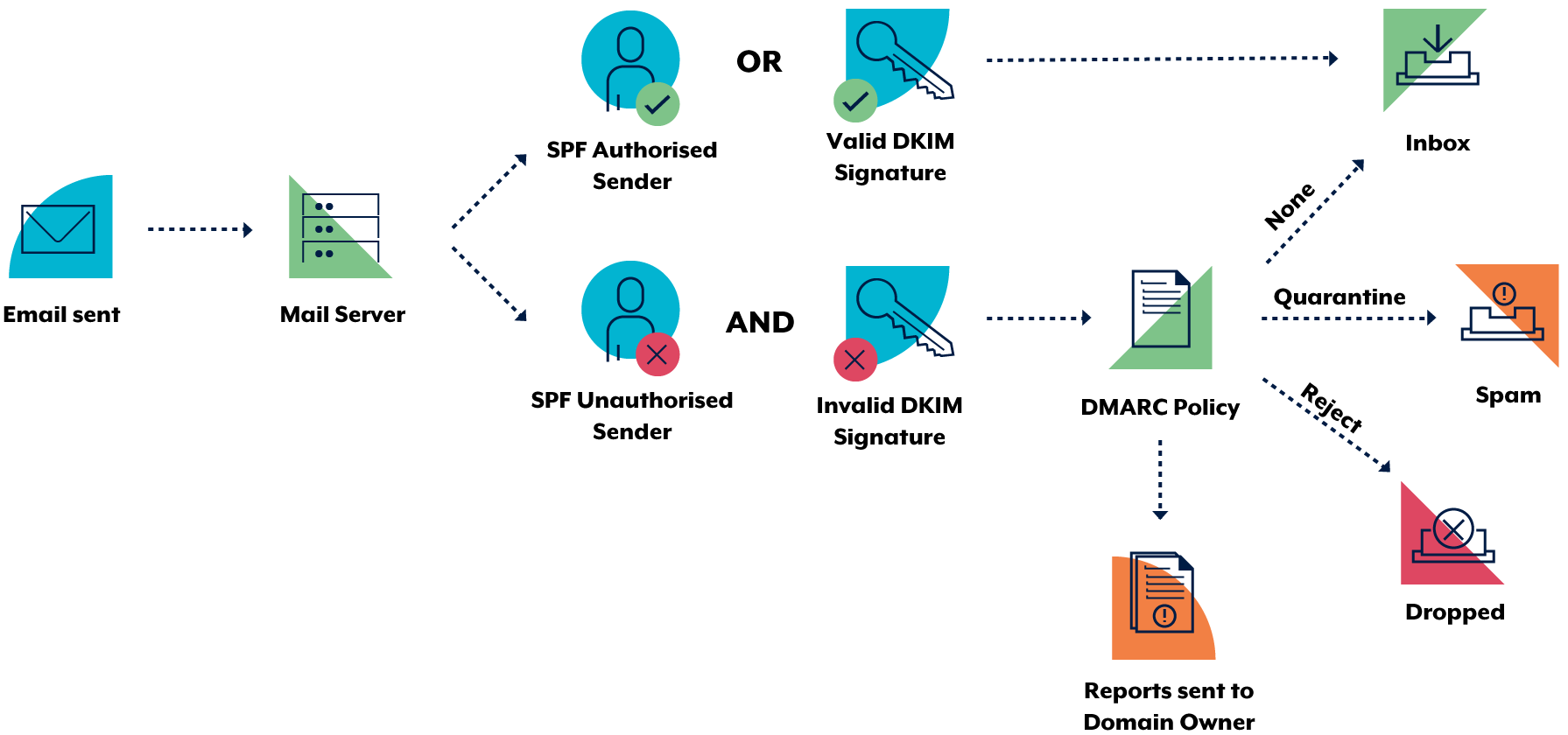
DMARC (Domain-based Message Authentication, Reporting and Conformance) is the most boring acronym ever, but it serves an important purpose. SPF's (and DKIM's for that matter) conformance and rejection specifications are loosely defined (due to the use of SHOULD rather than MUST in the RFCs), so various mail providers reject mail differently. DMARC was brought about to set definitive actions if mail were to fail SPF (or DKIM) checks[2], and provide reporting metrics for email administrators. DMARC records are a TXT record in the _dmarc. subdomain.
As these are simply TXT DNS records, they are easy to collect and analyse en-masse[3]. They also have a number of configuration options, simply implementing a record does not necessarily make it a secure one.
Collection
Alexa tracks which sites are visited most often, and publish a list of the top 1,000,000 websites. So I grabbed this list, pulled out all the .au sites, and trimmed it to the top 3000[4].
I then used a script[5] to pull the SPF and DMARC records (if present) for each domain, and used another script to pull out the following metrics.
Results
SPF
- 1965 domains (65.5%) had SPF records
- 1952 domains (65.1%) had valid SPF records
- 1301 domains (43.4%) had insecure SPF records
- 370 domains (12.3%) were overly permissive
- 1118 domains (37.3%) did not hard reject mail (
-all)
- 664 domains (22.1%) had a secure SPF record
DMARC
- 1601 domains (53.4%) had DMARC records
- 1601 domains (53.4%) had valid DMARC records
- 1575 domains (52.5%) had insecure DMARC records
- 127 domains (4.2%) had a relaxed SPF policy
- 191 domains (6.4%) had a relaxed DKIM policy
- 375 domains (12.5%) generated no reports
- 696 domains (23.2%) took no action (
p=none) - 375 domains (12.5%) only quarantine (
p=quarantine) - 62 domains (2.1%) did not check all mail (<
pct=100)
- 26 domains (0.8%) had a secure DMARC record
Analysis
Most of Australia's top 3,000 sites bothered to implement SPF and DMARC records. Clearly the knowledge in how to implement it, and the importance of implementation is there; just not the knowledge of the importance in fine-tuning their security; given that only 22% had secure SPF records, and less than 1% of domains had secure DMARC records.
Australian businesses are thus overwhelmingly exposed to the ever-increasing risk of email spoofing attacks; and the secure implementation of SPF and DMARC could see a large reduction in the $81 million lost by Australian businesses from email attacks every year.